Bring PHI Intelligence
to your
Experience Healthcare’s First PHI Security Intelligence Platform
Traditional security leaves
healthcare IT, security & privacy
teams asking…
-
Where is all
of our ePHI? -
Who/what has
access to ePHI? -
How can we
minimize risk?
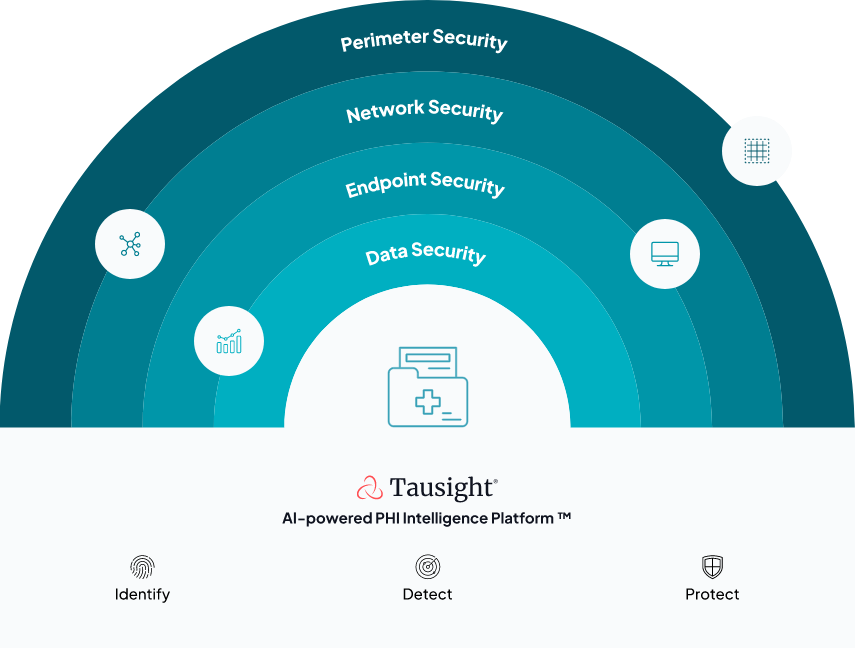
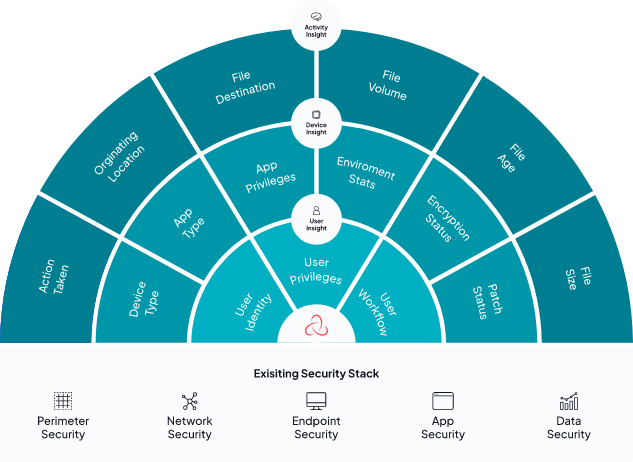
Tausight delivers unmatched visibility & intelligence into ePHI
Tausight’s healthcare data security platform is trained using a patented algorithm to find ePHI on devices, data stores and cloud assets. The result is powerful insights on the how PHI is being accessed, where it’s traveling, and how it might be at risk.
Integrated for
the uniqueness of healthcare.
Tausight is designed to fit into the unique, decentralized environments of healthcare. API integrations with leading security operations, ticketing and response systems enable automated protection of vulnerable ePHI.
Deployed in minutes…not months
Tausight’s cloud deployment and lightweight sensor can be installed in minutes, helping you discover ePHI in 60 minutes or less.
Immediate time to value
24/7 Availability w/Cloud-based SaaS
No deployment team needed
Reduce Risk, Liability & storage costs
