You can’t protect
what you can’t see.
Cybersecurity starts with data security visibility.
Cybersecurity starts with data security visibility.




Traditional cybersecurity is not designed to protect PHI and clinical workflows at the edge of decentralized, virtual healthcare. Securing healthcare has fundamentally changed.
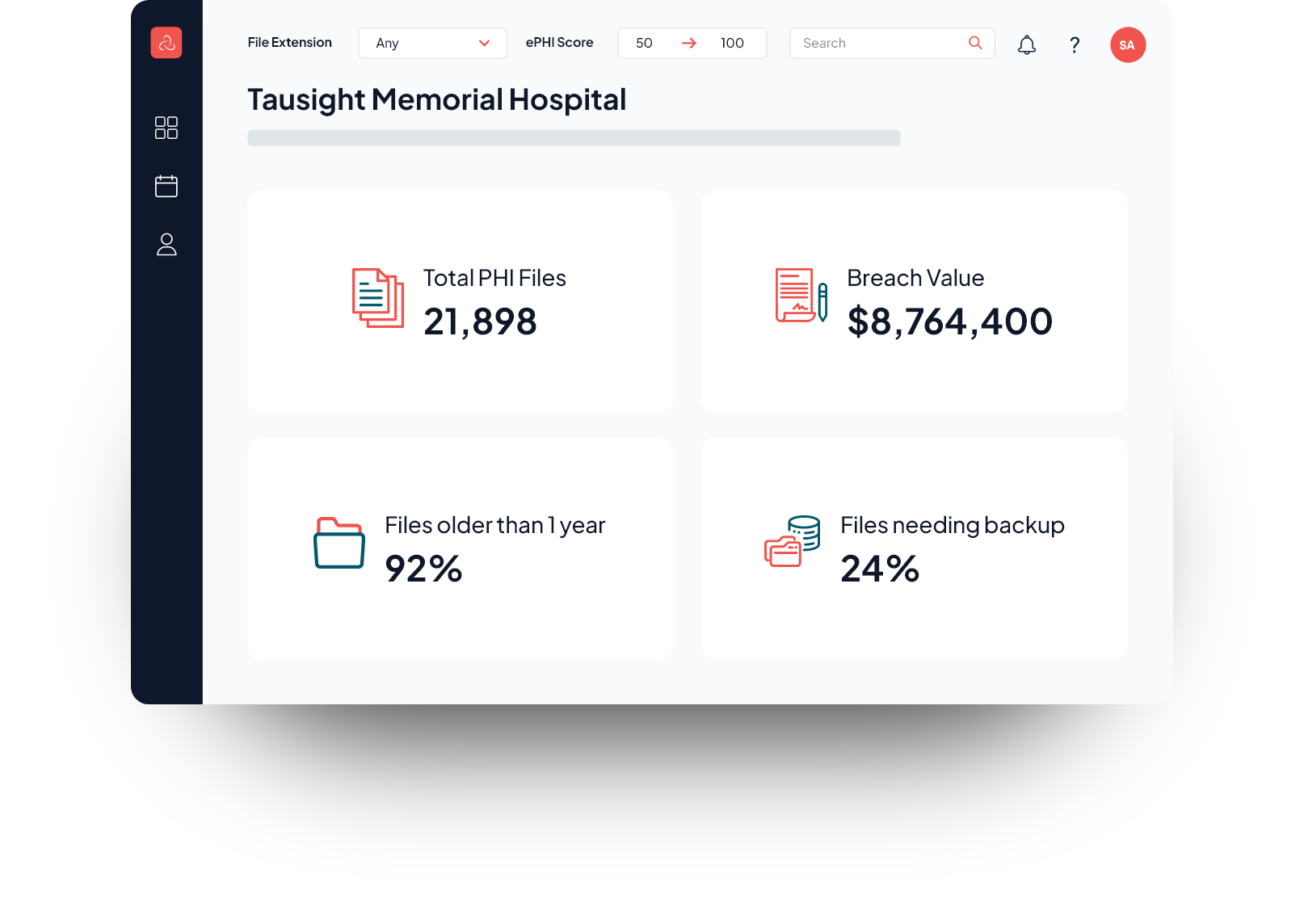
Inventory and identify your sensitive data (ePHI) to reduce your attack surface in case of an event.
Rapidly discover and identify top files and directories that had ePHI as part of your post-breach response.
Improve and prove compliance of your patient data for HIPAA, legal teams
and HHS.

ePHI Location and Detection.
Powered by the Tausight AI Model, Tausight can scan for ePHI insight across critical cloud and network infrastructure through an agentless executable. Upon downloading and running the Tausight PHI Locator, Tausight PHIL™, customers see real-time results within minutes.