Introducing Tausight®
The First Data Security Posture Management Platform
built for Healthcare
The First Data Security Posture Management Platform
built for Healthcare
“The foundation of HIPAA compliance is knowing everywhere within the organization where PHI or ePHI exists, on paper, or in digital form. With that understood, the organization must know how that PHI moves between those “at rest” locations. ”
Traditional cybersecurity is not designed to protect ePHI and clinical workflows at the edge of decentralized, virtual healthcare. Securing healthcare has fundamentally changed.
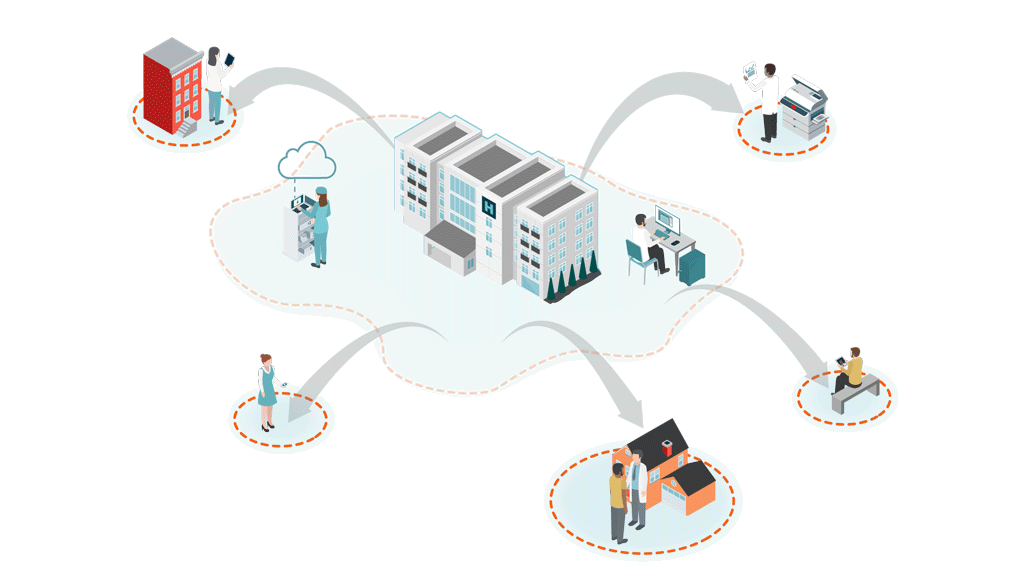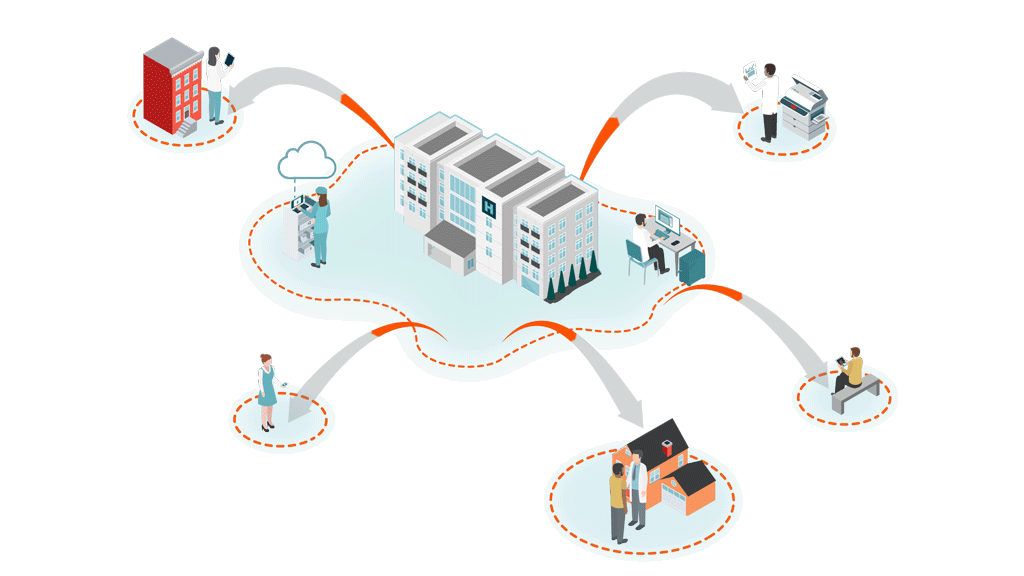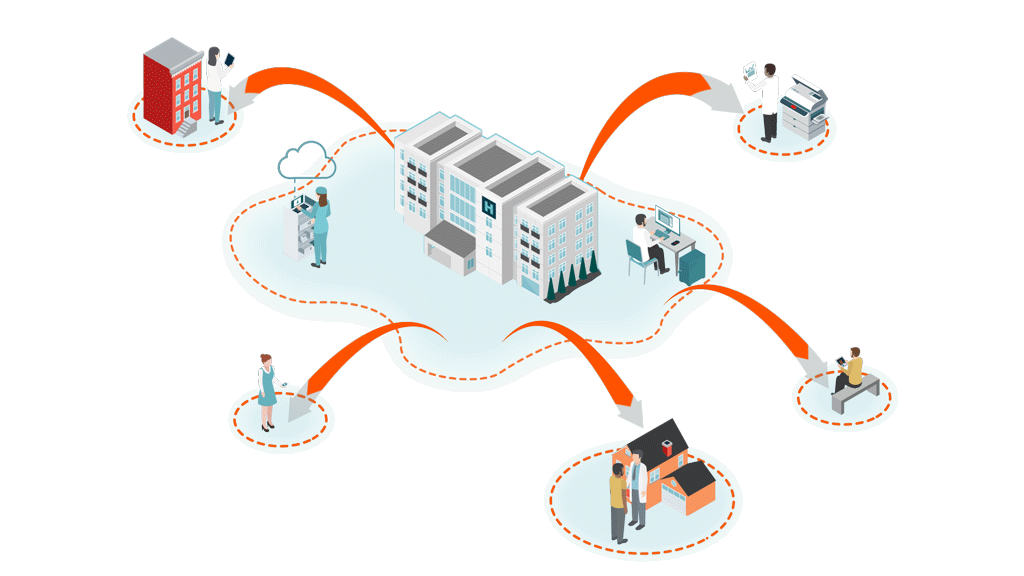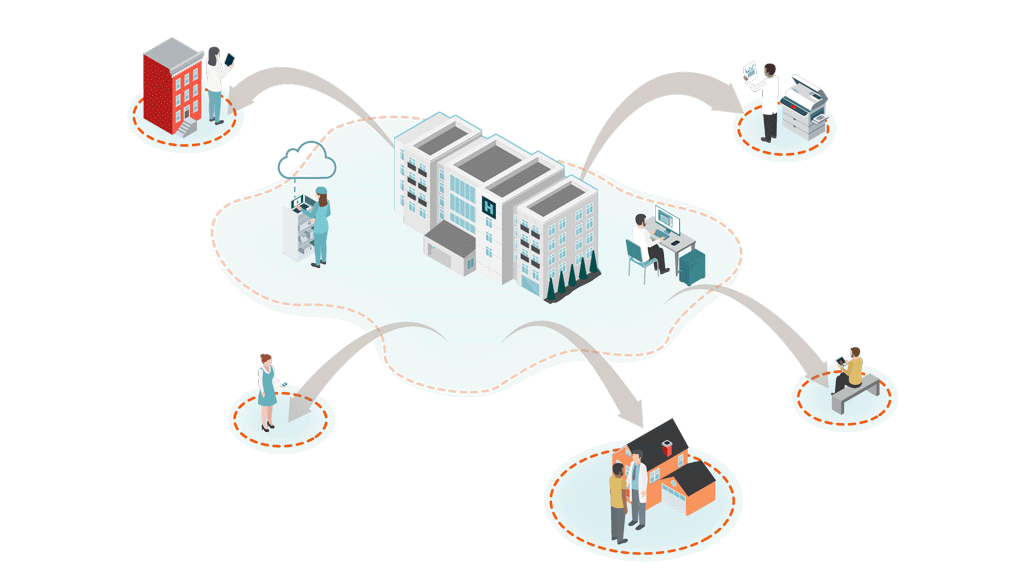
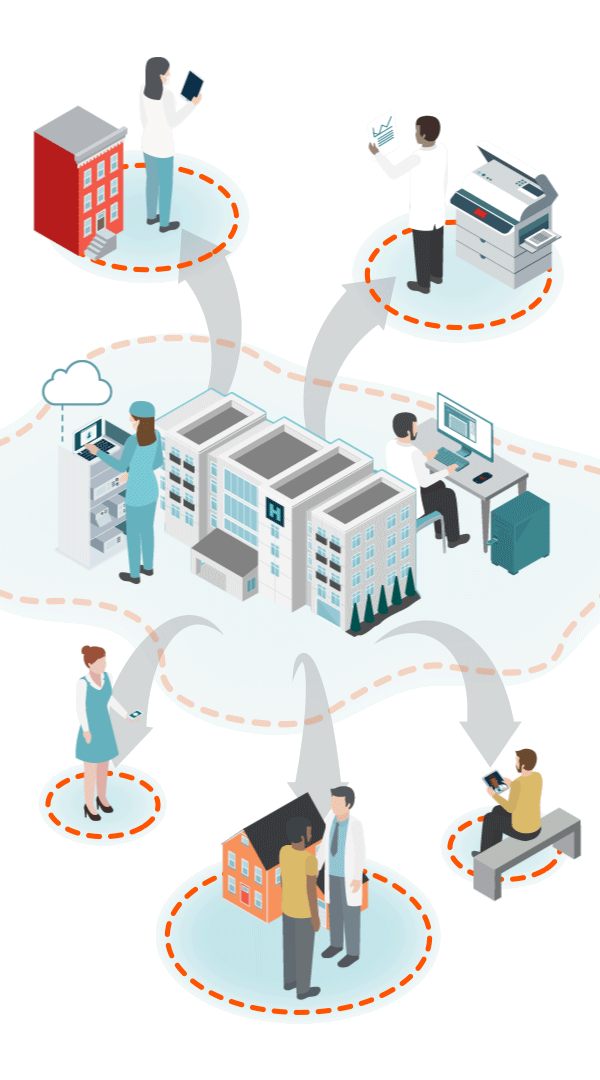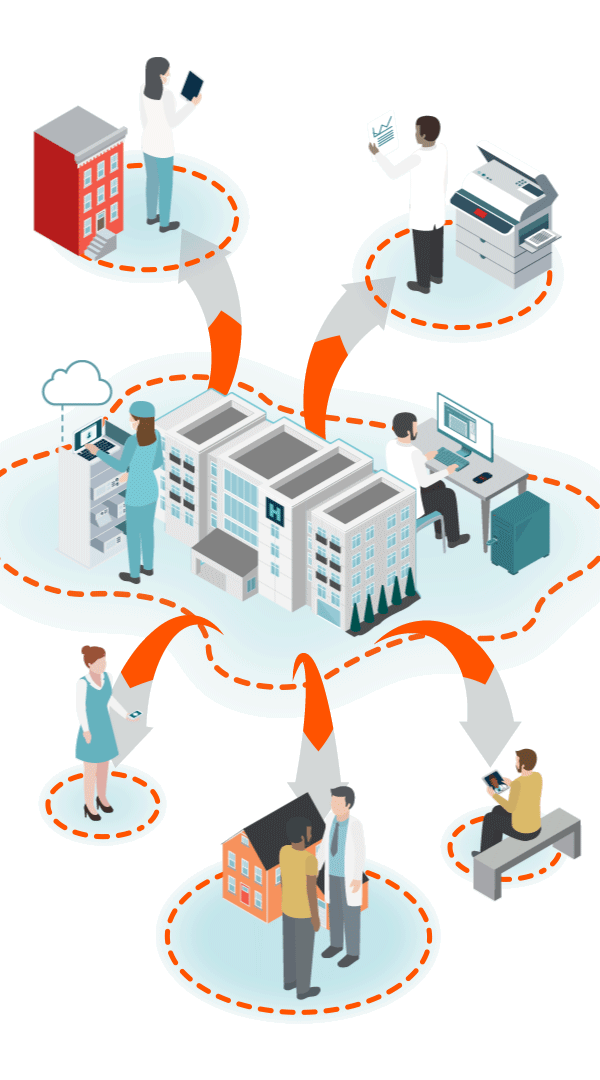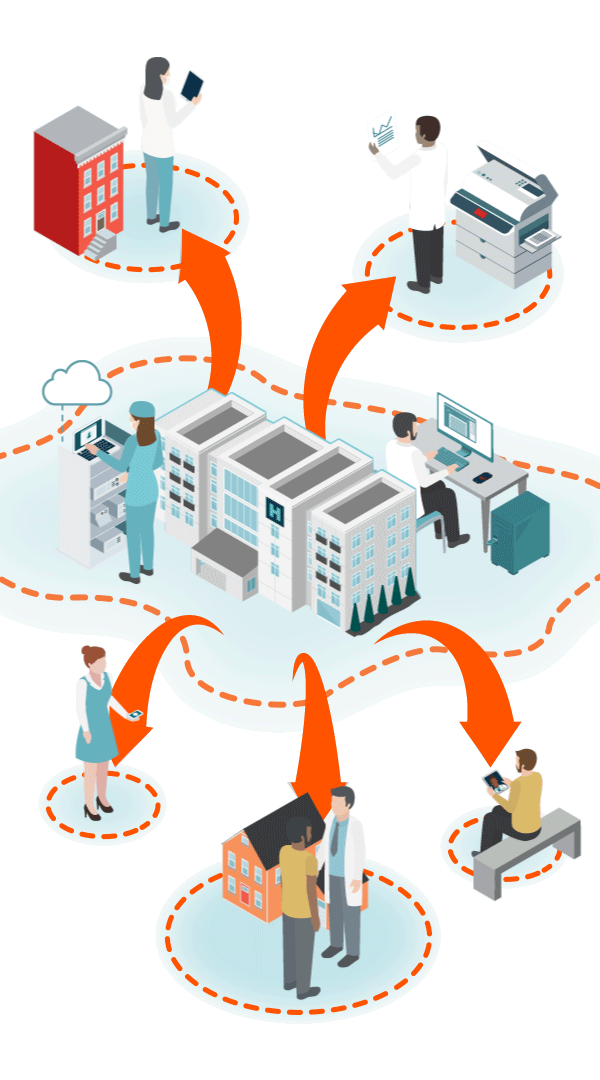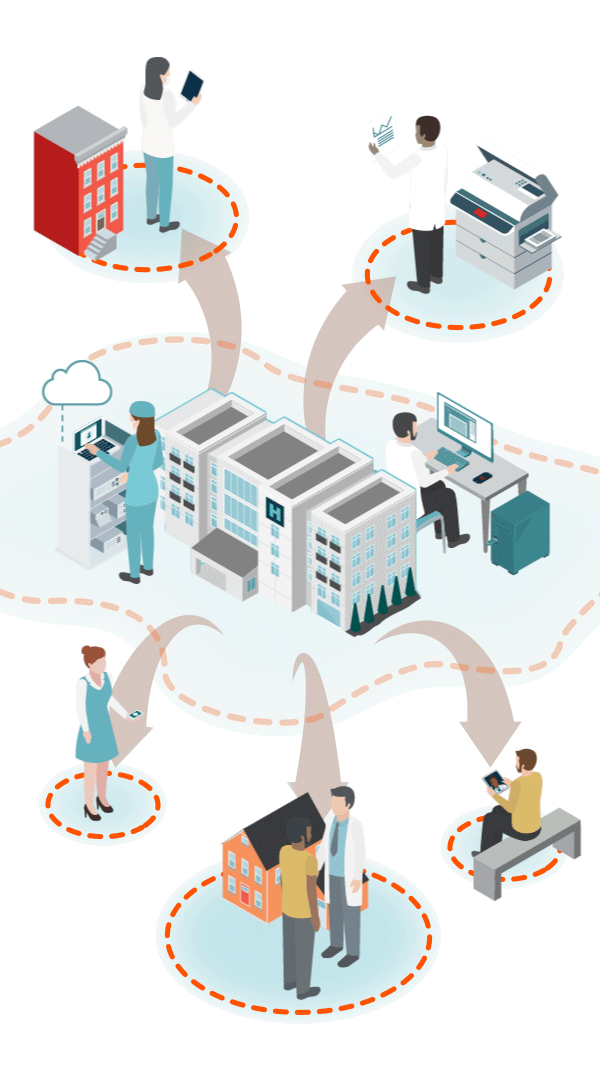
Unsecured, Private BA Clouds
(with unknown security standards)
Telehealth/Mobile
Cloud-based audio, video and data communications, telemetry data transmission, unsecure email and texts, smartphone apps and patient monitoring devices. All with limited IT security teams.
Hospital@Home
Patients at home create multiple new vulnerabilities via unsecure RPM, personal PCs/VPN, personal email, smart home devices, and unauthorized collaboration apps.
Interoperability & Data Exchange Outside Firewall
Shadow IT Apps & Personal Emails
Clinicians using personal email, messages, flash drives, cloud storage and unknown, unauthorized applications. 80% of employees create Shadow IT.
Remote First Care
Pandemic created an explosion of virtual endpoints, new attack surfaces and unknown, unsecure clouds.
Traditional cybersecurity is not designed to protect ePHI and clinical workflows at the edge of decentralized, virtual healthcare. Securing healthcare has fundamentally changed.
Clinicians are the new security perimeter.
Unsecured, Private BA Clouds
(with unknown security standards)
Hospital@Home
Patients at home create multiple new vulnerabilities via unsecure RPM, personal PCs/VPN, personal email, smart home devices, and unauthorized collaboration apps.
Shadow IT Apps & Personal Emails
Clinicians using personal email, messages, flash drives, cloud storage and unknown, unauthorized applications. 80% of employees create Shadow IT.
Telehealth/Mobile
Cloud-based audio, video and data communications, telemetry data transmission, unsecure email and texts, smartphone apps and patient monitoring devices. All with limited IT security teams.
Interoperability & Data Exchange Outside Firewall
Remote First Care
Pandemic created an explosion of virtual endpoints, new attack surfaces and unknown, unsecure clouds.
Traditional cybersecurity is not designed to protect ePHI and clinical workflows at the edge of decentralized, virtual healthcare. Securing healthcare has fundamentally changed.
Clinicians are the new security perimeter.
Unsecured, Private BA Clouds
(with unknown security standards)
Hospital@Home
Patients at home create multiple new vulnerabilities via unsecure RPM, personal PCs/VPN, personal email, smart home devices, and unauthorized collaboration apps.
Shadow IT Apps & Personal Emails
Clinicians using personal email, messages, flash drives, cloud storage and unknown, unauthorized applications. 80% of employees create Shadow IT.
Telehealth/Mobile
Cloud-based audio, video and data communications, telemetry data transmission, unsecure email and texts, smartphone apps and patient monitoring devices. All with limited IT security teams.
Interoperability & Data Exchange Outside Firewall
Remote First Care
Pandemic created an explosion of virtual endpoints, new attack surfaces and unknown, unsecure clouds.
Tausight uses machine learning and natural language processing
to automate ePHI detection and compliance.
An ePHI-centric way to simplify alignment and reporting on 405(d) Healthcare Industry Cybersecurity Practices (HICP)

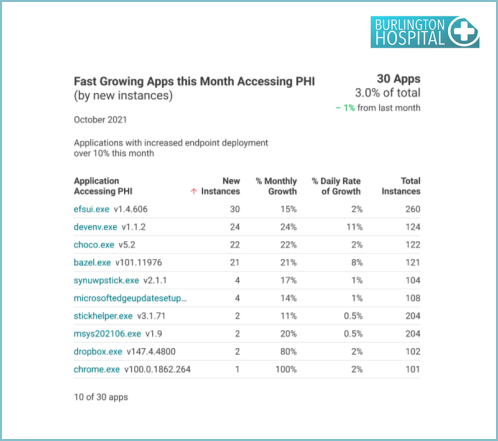
Reports to support Endpoint Protection Systems include Audit endpoint encryption, Endpoint OS patch assessment, Local admin access, Fastest growing applications, Low usage applications. Some examples include: 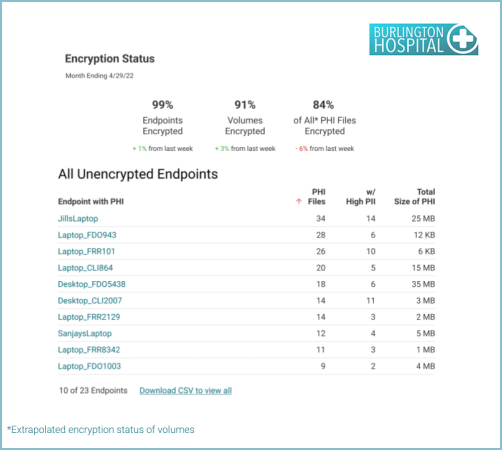
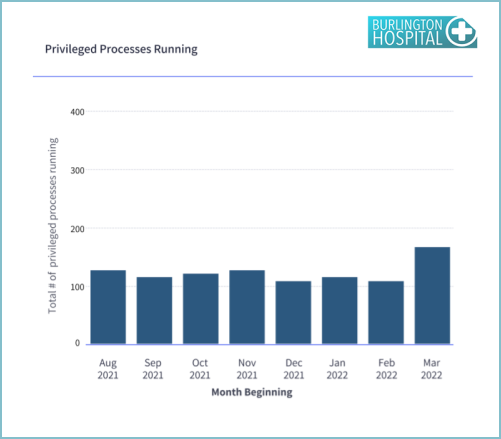
Reports related to Identity and Access Management include: Users with privileged access and Change in privileged processes running. Here are samples… 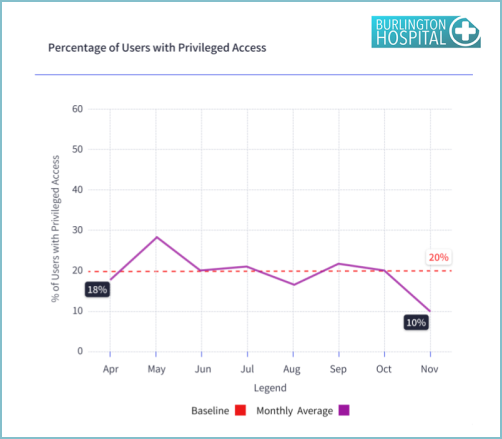
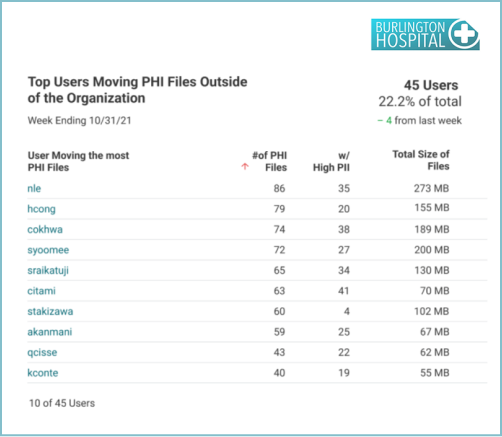
Reports to support Data Protection and Loss Prevention include PHI moving outside of the network, Audit location of external movement, Establish baseline for PHI emailed, Top users sending PHI, PHI movement to removable media, Audit file transfer URLs. Some examples include: 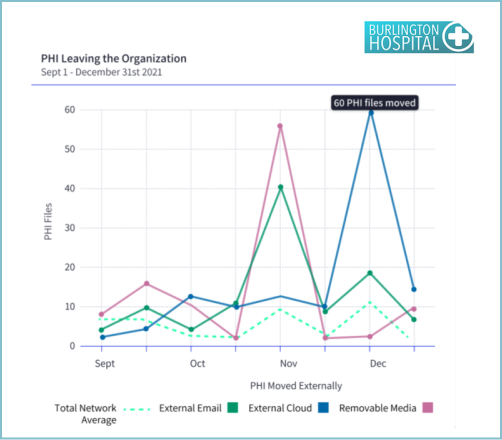
Covering IT Asset Management is the report Endpoint activity 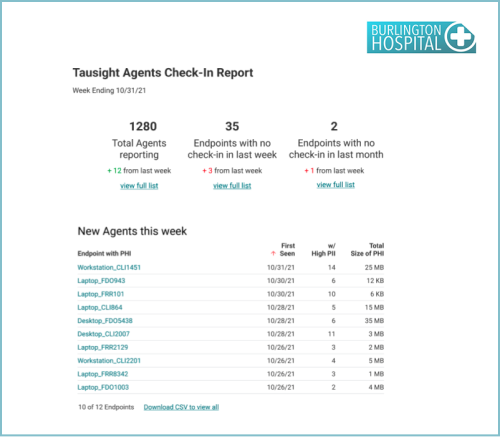
The ability to know where ePHI lives, where it’s being moved to, who it’s being shared with, and having confidence that it is secured and well managed to minimize risk and exposure for your patients and organization.
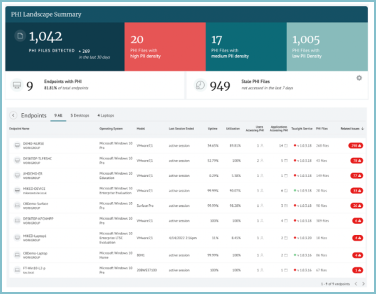

Reports to support Vulnerability Management include Endpoint patch assessment Summary, Endpoint patch assessment – Installation Lag, Endpoint patch assessment – Histogram, Endpoint patch assessment – Critical patches, Endpoint patch assessment – non-critical patches, Chrome patch assessment and Edge patch assessment. Some examples include: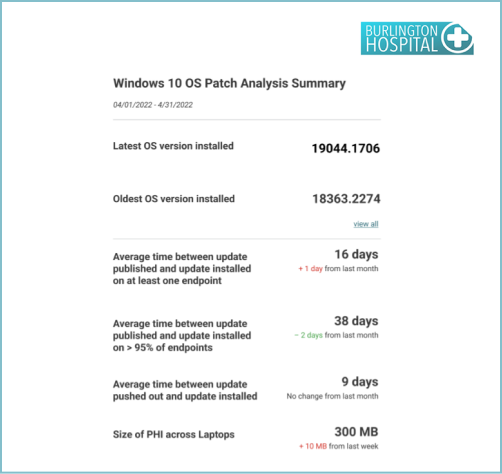
Reports to support Security Operations Center and Incident Response include Lost / stolen laptop and User litigation. Some examples include:
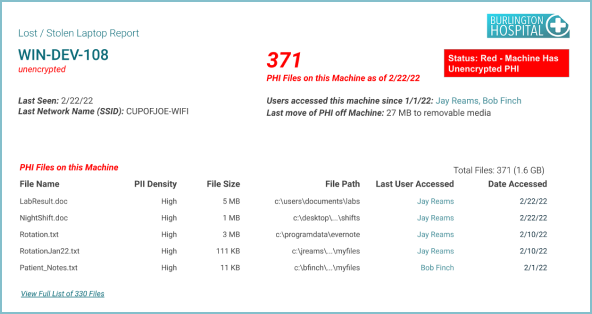
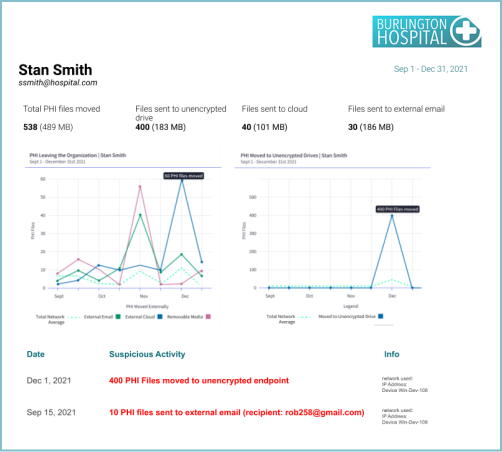


An ePHI-centric way to simplify alignment and reporting on 405(d) Healthcare Industry Cybersecurity Practices (HICP)

Reports to support Endpoint Protection Systems include Audit endpoint encryption, Endpoint OS patch assessment, Local admin access, Fastest growing applications, Low usage applications. Some examples include:


Reports related to Identity and Access Management include: Users with privileged access and Change in privileged processes running. Here are samples…


Reports to support Data Protection and Loss Prevention include PHI moving outside of the network, Audit location of external movement, Establish baseline for PHI emailed, Top users sending PHI, PHI movement to removable media, Audit file transfer URLs. Some examples include:


Covering IT Asset Management is the report Endpoint activity

The ability to know where ePHI lives, where it’s being moved to, who it’s being shared with, and having confidence that it is secured and well managed to minimize risk and exposure for your patients and organization.


Reports to support Vulnerability Management include Endpoint patch assessment Summary, Endpoint patch assessment – Installation Lag, Endpoint patch assessment – Histogram, Endpoint patch assessment – Critical patches, Endpoint patch assessment – non-critical patches, Chrome patch assessment and Edge patch assessment. Some examples include:

Reports to support Security Operations Center and Incident Response include Lost / stolen laptop and User litigation. Some examples include:




An ePHI-centric way to simplify alignment and reporting on 405(d) Healthcare Industry Cybersecurity Practices (HICP)
The ability to know where ePHI lives, where it’s being moved to, who it’s being shared with, and having confidence that it is secured and well managed to minimize risk and exposure for your patients and organization.


Reports to support Endpoint Protection Systems include Audit endpoint encryption, Endpoint OS patch assessment, Local admin access, Fastest growing applications, Low usage applications. Some examples include:


Reports related to Identity and Access Management include: Users with privileged access and Change in privileged processes running. Here are samples…


Reports to support Data Protection and Loss Prevention include PHI moving outside of the network, Audit location of external movement, Establish baseline for PHI emailed, Top users sending PHI, PHI movement to removable media, Audit file transfer URLs. Some examples include:


Covering IT Asset Management is the report Endpoint activity


Reports to support Vulnerability Management include Endpoint patch assessment Summary, Endpoint patch assessment – Installation Lag, Endpoint patch assessment – Histogram, Endpoint patch assessment – Critical patches, Endpoint patch assessment – non-critical patches, Chrome patch assessment and Edge patch assessment. Some examples include:

Reports to support Security Operations Center and Incident Response include Lost / stolen laptop and User litigation. Some examples include:




Tausight Provides Situational PHI Awareness
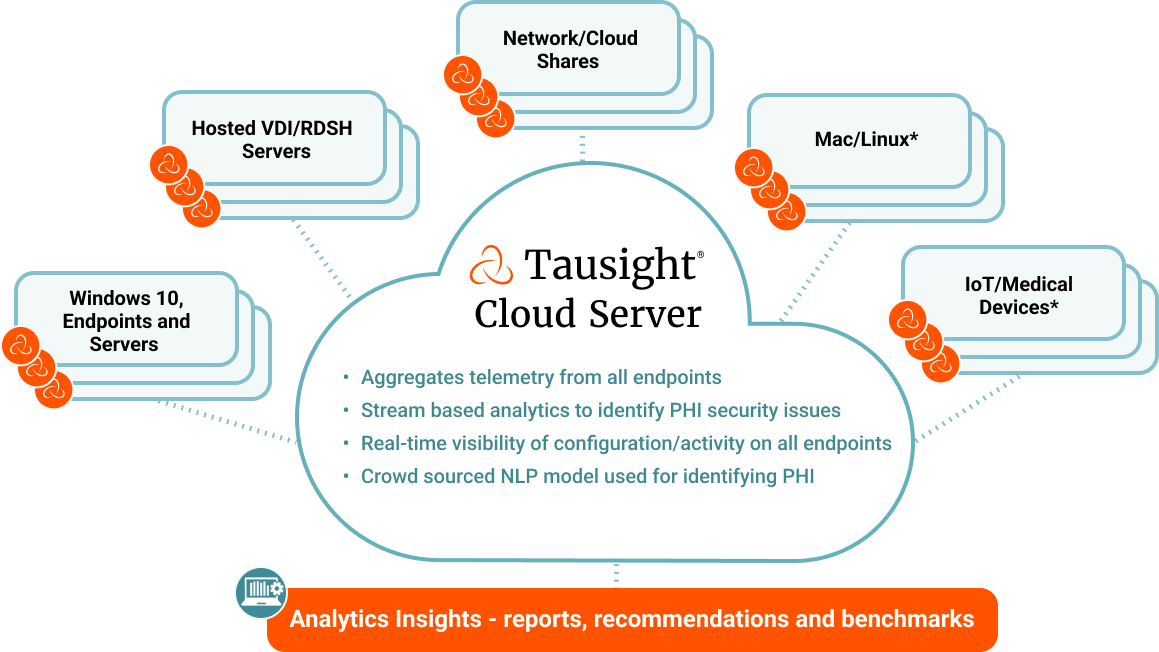

Start securing ePHI and protect clinicians at risk.
“Cyber resiliency is the new norm. Business continuity requires securing your ePHI clinical workflow.”
– Cybersecurity Task Force
Be the first to learn how Tausight can discover and protect ePHI at the point of risk. Connect with a Tausight platform expert to start your journey today:


